- Home
- People
- Projects
- Practical Security Verification
- Secure Cloud Computing
- Security of AI Systems
- Deep Learning for Security
- Smartphone Security
- Cache Side-Channels and Secure Caches
- De-anonymization
- Running Unvetted Programs
- Secure RISC-V processor
- SP and Bastion Secure Processor Architectures
- Crypto Acceleration
- OpenSPARC Researh
- SecureCore
- Advanced Bit Manipulation
- PAX
- PLX
- Publications
- Research
- Conference and Journals
- Project Archive
- Photos
Secure Cloud Computing
Secure Cloud Computing Overview
We focus on designing secure cloud architectures to provide various protections for Virtual Machines in Infrastructure as a Service (IaaS) systems. These projects include:
- The Cloud Security on Demand architecture that enables different security services for Virtual Machines in cloud computing.
- The CloudMonatt architecture that monitors and attests the security health of cloud servers.
- The NoHype and Hyperwall architectures which protect Virtual Machines from a compromised hypervisor
- The Pwnetizer architecture for fast Virtual Machine cloning.
Cloud Security on Demand
Cloud customers need guarantees regarding the security of their virtual machines (VMs), operating within an Infrastructure as a Service (IaaS) cloud system. This is complicated by the customer not knowing where his VM is executing, and on the semantic gap between what the customer wants to know versus what can be measured in the cloud. We present an architecture for monitoring a VM’s security health, with the ability to attest this to the customer in an unforgeable manner
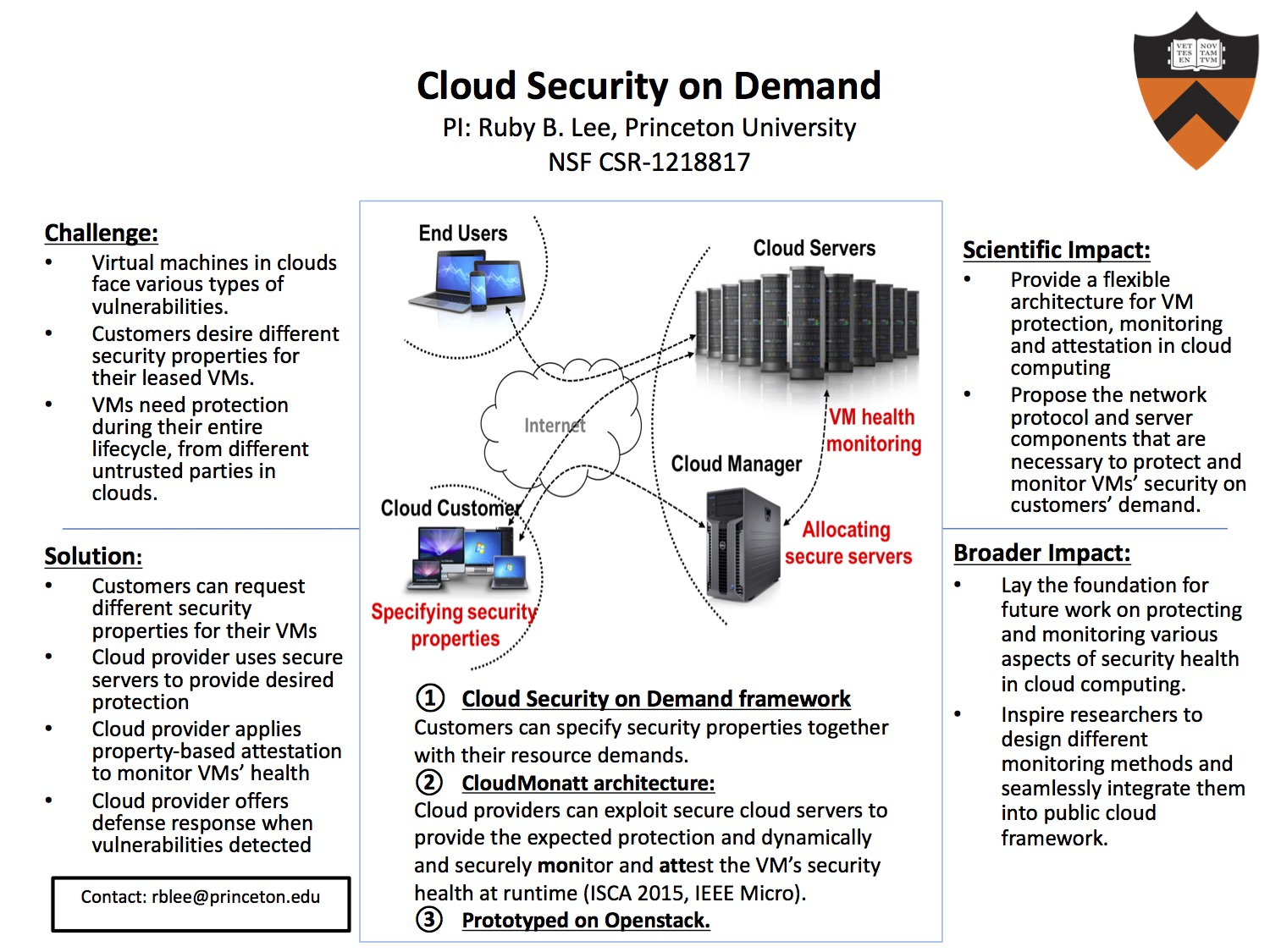
- Tianwei Zhang and Ruby B. Lee " Monitoring and Attestation of Virtual Machine Security Health in Cloud Computing". IEEE Micro Special Issues on Security, Volume 36, Issue 5, 2016
- Tianwei Zhang and Ruby B. Lee, " CloudMonatt: an Architecture for Security Health Monitoring and Attestation of Virtual Machines in Cloud Computing". In ACM International Symposium on Computer Architecture (ISCA), 2015.
- Pramod Jamkhedkar, Jakub Szefer, Diego Perez-Botero, Tianwei Zhang, Gina Triolo and Ruby B. Lee, " A Framework for Realizing Security on Demand in Cloud Computing", in IEEE International Conference on Cloud Computing Technology and Science (CloudCom), 2013
Secure Cloud Computing Servers
Hypervisor-Free Vritualization
Cloud computing is a disruptive trend that is changing the way we use computers and virtualization is the key underlying technology in cloud infrastructures. Unfortunately, the use of virtualization is the source of a significant security concern: multiple virtual machines (VMs) run on the same server and since the virtualization layer plays a considerable role in the operation of a virtual machine, a malicious VM has the opportunity to attack the virtualization layer. A successful attack would give the malicious VM control over the all-powerful virtualization layer and potentially compromise the confidentiality and integrity of the virtualization layer and the other VMs. The NoHype system architecture proposes removing the virtualization layer while retaining the key features needed to be able to provide for multi tenancy of VMs. The NoHype architecture is named to indicate the removal of the hypervisor (no hypervisor) but we also try to show that the NoHype architecture may indeed be implementable on today's commodity hardware (not a hype). By removing bulky virtualization layer we propose that the architecture improves security while retaining key functionality to be able to host multiple VMs on same physical hardware.
This is a joint work between Prof. Lee's group and Prof. Rexford's group (CS department).
- Eric Keller, Jakub Szefer, Jennifer Rexford, and Ruby B. Lee, "NoHype: Virtualized cloud infrastructure without the virtualization," in proceedings of the International Symposium on Computer Architecture (ISCA 2010), pages 350-357, June 2010.
- Jakub Szefer, Eric Keller, Ruby B. Lee and Jennifer Rexford, "Eliminating the Hypervisor Attack Surface for a More Secure Cloud," to appear in Proceedings of the Conference on Computer and Communications Security (CCS 2011), October 2011.
Hypervisor-Secure Virtualization
Virtualization has become a standard part of many computer systems. A key part of virtualization is the all-powerful hypervisor which manages the physical platform and can access all of its resources, including memory assigned to the guest virtual machines (VMs). Continuing releases of bug reports and exploits in the virtualization software show that defending the hypervisor against attacks is very difficult. In this work, we present hypervisor-secure virtualization – a new research direction with the goal of protecting the guest VMs from an untrusted hypervisor. We also present the Hy- perWall architecture which achieves hypervisor-secure virtualization, using hardware to provide the protections. HyperWall allows a hypervisor to freely manage the memory, processor cores and other resources of a platform. Yet once VMs are created, our new Confidentiality and Integrity Protection (CIP) tables protect the memory of the guest VMs from accesses by the hypervisor or by DMA, depending on the customer’s specification. If a hypervisor does become compromised, e.g. by an attack from a malicious VM, it cannot be used in turn to attack other VMs. The protections are enabled through minimal modifications to the micropro- cessor and memory management units. Whereas much of the previous work concentrates on protecting the hypervisor from attacks by guest VMs, we tackle the problem of protecting the guest VMs from the hypervisor.
- Jakub Szefer and Ruby B. Lee, "Architectural Support for Hypervisor-Secure Virtualization," in Proceedings of the International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS), March 3–7, 2012.
- Jakub Szefer and Ruby B. Lee, "A Case for Hardware Protection of Guest VMs from Compromised Hypervisors in Cloud Computing," in Proceedings of the Second International Workshop on Security and Privacy in Cloud Computing (SPCC), June 20-24, 2011.
Other related papers
- Jakub Szefer, Pramod Jamkhedkar, Yu-Yuan Chen and Ruby B. Lee, "Physical Attack Protection with Human-Secure Virtualization in Data Centers ," in IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), 2012.
- Jakub Szefer, "Architectures for Secure Cloud Computing Servers," PhD Thesis, Electrical Engineering Department, Princeton University, Princeton, NJ, 2013.
Hypervisor Vulnerabilities
The rise of the Cloud Computing paradigm has led to security concerns, taking into account that resources are shared and mediated by a Hypervisor which may be targeted by rogue guest VMs and remote attackers. In order to better define the threats to which a cloud server’s Hypervisor is exposed, we conducted a thorough analysis of the codebase of two popular open-source Hypervisors, Xen and KVM, followed by an extensive study of the vulnerability reports associated with them. Based on our findings, we propose a characterization of Hypervisor Vulnerabilities comprised of three dimensions: the trigger source (i.e. where the attacker is located), the attack vector (i.e. the Hypervisor functionality that enables the security breach), and the attack target (i.e. the runtime domain that is compromised). This can be used to understand potential paths different attacks can take, and which vulnerabilities enable them. Moreover, most common paths can be discovered to learn where the defenses should be focused, or conversely, least common paths can be used to find yet-unexplored ways attackers may use to get into the system
- Diego Perez-Botero, Jakub Szefer and Ruby B. Lee, "Characterizing Hypervisor Vulnerabilities in Cloud Computing Servers," in Proceedings of the Workshop on Security in Cloud Computing (SCC), 2013.
- Diego Perez-Botero, "Pwnetizer: Improving Availability in Cloud Computing Through Fast Cloning and I/O Randomization," MSE Thesis, Computer Science Department Department, Princeton University, Princeton, NJ, 2013.
Other Cloud Computing Papers
- Jakub Szefer and Ruby B. Lee, "BitDeposit: Deterring Attacks and Abuses of Cloud Computing Services Through Economic Measures," in Proceedings of the Workshop on Assured Cloud Computing (ACC), 2013.
